 As you may or may not know, Filezilla, the extremely popular FTP client, stores all of your FTP passwords in plain text on your hard drive. While I strongly disagree with this practice, I also understand that there are reasons not to do so. It would be really nice to have some sort of option to encrypt the passwords, but I don’t see that happening any time in the near future.
As you may or may not know, Filezilla, the extremely popular FTP client, stores all of your FTP passwords in plain text on your hard drive. While I strongly disagree with this practice, I also understand that there are reasons not to do so. It would be really nice to have some sort of option to encrypt the passwords, but I don’t see that happening any time in the near future.
There are actually multiple levels of danger in using Filezilla (and, presumably, many other FTP clients). Unlike a Web browser, where, if you choose not to use the password manager none of your passwords are stored; Filezilla still stores all of the details from your most recent connection in a file called filezilla.xml and all of the details from your 10 most recent connections (at least, the ones you make by typing the information into the Filezilla interface; which is the only way to connect if you are not using the Site Manager) in a file called recentservers.xml, even if you choose not to use the Site Manager. These are plain old XML files with all of the information stored in plain, non-encrypted text. The format of the entries looks similar to the following.
<Server>
<Host>example.com</Host>
<Port>22</Port>
<Protocol>1</Protocol>
<Type>0</Type>
<User>username</User>
<Pass>password</Pass>
<Logontype>1</Logontype>
<TimezoneOffset>0</TimezoneOffset>
<PasvMode>MODE_DEFAULT</PasvMode>
<MaximumMultipleConnections>0</MaximumMultipleConnections>
<EncodingType>Auto</EncodingType>
<BypassProxy>0</BypassProxy>
</Server>As you can imagine, this poses a serious potential security risk.
What’s The Solution?
Unfortunately, there isn’t really an ideal solution. I would imagine that any FTP program is going to be vulnerable to various security holes no matter what; and the more convenient the program is to use, the more potential holes there will be.
However, there are two potential methods you can use to try to make things a little more secure.
The first is described in a post from Stellar Web Works, in which Aidan Curran explains how to use a password management program to store your information, and send it to Filezilla automatically. The important part of this process is to throw Filezilla into “kiosk mode”, which stops it from storing any of the information from your recent connections.
The other option is to encrypt the stored data yourself, using a program like TrueCrypt. You can do this by following these simple steps:
- Download and install TrueCrypt (available for Windows, Mac and Linux).
- Open TrueCrypt and press the Create Volume button.
- Select the most appropriate option (in most cases, you’ll just want to use the “Create an encrypted file container” option – for purposes of this tutorial, this is the option that was chosen).
- Choose whether you want this volume to be a standard volume or a hidden volume (which is protected by two separate passwords – one to unencrypt a false container and a second to unencrypt the true container).
- Click the “Select File” button, navigate to the area on your hard drive in which you want the file to be stored. Type a filename (whatever you want it to be) into the filename box and press the “Save” button.
- Choose encryption and hashing algorithms. Whatever you choose should be just fine.
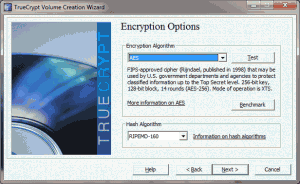
- Decide how large you want the file to be (for the purposes of this tutorial, the file doesn’t need to be larger than a 100-200 kilobytes, but if you want to store other files in this area, you should choose whatever size you want – these containers cannot be easily resized, so make sure it’s big enough from the beginning).
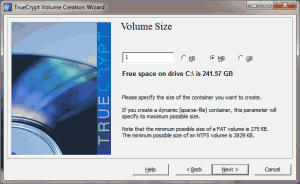
- If you choose a large enough filesize, TrueCrypt will ask whether or not you plan to store large files (greater than 4 gigs) in the volume (not shown).
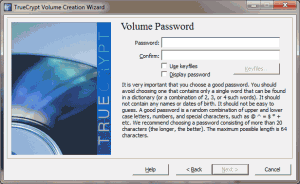
- Enter the password that you want to use to encrypt/decrypt the data. TrueCrypt recommends that you use a password at least 20 characters long (and will throw a dismissable warning message if you use a shorter password).
- Choose the appropriate filesystem (in most cases, you can leave this set to the default that TrueCrypt uses) and click the “Format” button.
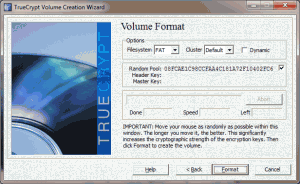
Once you’ve followed those steps, you will officially have an encrypted file container on your hard drive. Any items you store in that container will be encrypted and decrypted on-the-fly by TrueCrypt. The next thing you need to do is to mount your new file container.
- Open TrueCrypt.
- Choose an available drive letter from the list (make sure you choose one that will consistently be available on your computer).
- Click the “Select File” button and locate the file container you created.
- Click the “Mount” button.
- Enter the password you used when creating the volume.
- Press the Exit button to minimize/hide TrueCrypt.
- Navigate to the drive you used to mount the volume.
Once there, you can create a new folder (like “filezilla”). Then, figure out where Filezilla is currently storing your configuration files.
On Windows XP, they are located in C:\Documents and Settings\USERNAME\Application Data\filezilla. On Windows 7, they are located in C:\Users\USERNAME\AppData\Roaming\Filezilla. I don’t, offhand, know where the files are stored on Linux or Mac, but I’m sure the paths are probably fairly similar.
You’ll then want to copy all of the files from that folder and paste them into the folder you just created within your encrypted volume; and then delete the originals.
Locate the Filezilla program on your hard drive, create a new XML file in that folder called fzdefaults.xml, paste in the following code, modify the value of the “Config Location” element and save it.
<FileZilla3>
<Settings>
<Setting name="Config Location">D:/filezilla/</Setting>
<Setting name="Kiosk mode">0</Setting>
<Setting name="Disable update check">0</Setting>
</Settings>
</FileZilla3>From that point forward, Filezilla will begin using your encrypted file container as the location for its configuration files. Any server addresses, usernames and passwords saved by Filezilla will be saved there, instead of in the default location.
Important Note
Once you do this, you will need to make sure your encrypted volume is mounted before you start Filezilla. If you don’t, Filezilla will pop up a series of about 10 or 15 error alerts in a row, followed by 2 or 3 more when you try to do anything in the program, followed by about 5 more when you close the program (most indicating that Filezilla couldn’t write to the non-existent settings files).
Extreme Solution
Of course, if you only have one or two websites to which you connect with Filezilla or you are really, really good at remembering passwords and config settings, you could always run Filezilla in “kiosk mode” all the time.
3 Responses
At the end, using truecrypt is not secure. When you have connected truecrypt, every trojan can read out the settings. Using a password program like KeyPass is much more secure.
When using KeyPass, though, aren’t the commands sent in plain text to the command line (which, I would assume, can be read by any of the trojans as well)?
I recommend use Gnome for FTP tranfers.
Any soft on Windows became usecure, not for the software, indeen the O.S.
Thanks for post.
L.